solution(290)


FREE Bionics Taiwan Inc.
857
0
Smart Healthcare
Data-oriented robotics exoskeleton rehabilitation system
FREE Bionics offers the world's first exoskeleton robotic rehabilitation system consists mainly of the joint activity training robot "NimBO", and the lower limb exoskeleton robot "FREE Walk". Which integrates precise data analysis to form a comprehensive and precise rehabilitation solution driven by data.
NimBO is apply on measuring movement angles and muscle strength of six major joints of the patient's upper/lower limbs, analyzing the bottleneck of the patient's movement ability, and then to guide the patient to conduct correct movement training to improve joint mobility.
In addition, FREE Walk provides patients with functional movement needs of the lower limbs. The power assistance and movement guidance allow patients to perform nerve reshaping of lower limb movements and core training of the trunk, which can significantly improve mobility for patients in both acute and chronic stages.
This system shows significant improvement in mobility for both acute and chronic patients.


Billion Watts Technologies Co., Ltd.
78
0
Smart Energy Storage
Solar Energy Storage Microgrid Solutions
Billion Electric Group , in collaboration with Taiwanese partners, has successfully deployed 495 kWp of solar PV and 1,997 kWh of battery energy storage systems (BESS) in Palau, Tuvalu, and the Marshall Islands. These modular microgrids reduce reliance on imported fossil fuels, ensuring stable green energy supply for agriculture, aquaculture, and local communities. The project is expected to cut carbon emissions by 800 metric tons annually, with over 50% renewable energy self-sufficiency at aquaculture centers and demonstration farms. Meanwhile, livestock farms, offices, and dormitories now operate on 100% green energy, significantly lowering both energy costs and environmental impact.
Billion Electric Group provides end-to-end energy solutions, from R&D and manufacturing to system integration and deployment. The project features MIT ( Made In Taiwan) renewable energy technologies, including Billion’s Fusio series BESS, Giga series PV inverters, and an AI-driven EMS (Energy Management System). The system enables real-time power optimization, bidirectional energy transmission, and cloud-based monitoring platform, significantly enhancing grid stability and energy efficiency.


Owlsome Tech
332
1
AI / AIoT
LiftMind - Elevator AIoT Retrofit System
LiftMind is a non-invasive AIoT elevator add-on system that enables rapid upgrades to smart functionality without modifying existing elevator control systems. The system leverages advanced external sensors and AI technology to deliver features such as passenger flow monitoring, emergency incident alerts, user behavior analysis, elevator operation optimization, and enhanced, user-friendly riding experiences. Its open architecture seamlessly integrates with Building Management Systems (BMS) and other IoT devices, significantly improving elevator management efficiency and user satisfaction. LiftMind supports a wide range of elevator brands and models, offering flexible adaptability to various application scenarios, making it the ideal solution for smart building upgrades.

TECO
2.01k
0
Smart Transportation
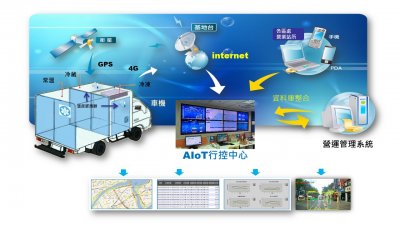
AI Video Control Center
ITTS Smart Logistics Solution-AI Video Control Center, from the perspective of practitioners, uses a smart management system to help the logistics company master the three major information of people, vehicles and parcel.
The main features are:
APP-based mobile control, Smart phones can provide anytime & anywhere control capability
Dynamics Video + image real-time monitoring, real-time conditions of vehicles moving and stopping are clearly visible
Visualization of data reports, clear operational information such as fuel consumption rate and delivery rate at a glance
AI intelligent interpretation, real-time reminder for driving violation judgment, reduce the violation rate, and provide a safe driving environment
The accumulation of AI machine learning can be extended to several aspects in the future:
For drivers-through driving behavior interpretation, the driver's condition can be found immediately to prevent dangerous driving; automatic routing suggestions to help novice drivers quickly get started and reach the level of mature delivery
The city management can share real-time road conditions images or video, reflect road level and post-disaster road conditions, and street management capabilities
Provide scientific and technological law enforcement capabilities to localities-image recording of license plate recognition can assist police units in investigating cases


Far EasTone Telecommunications Co., Ltd.
14.79k
3
5G Telecommunication
5G Smart Manufacturing
The power of 5G opens new opportunities for manufacturing upgrades. FET integrates Big data, AI and IoT technologies to build the first “5G Smart Factory” in Taiwan. We provide comprehensive smart manufacturing solutions from IT to OT, accelerating the progress towards Intelligent Manufacturing!
Features
* 5G Private Network as a Service:Enhancing network security with MEC, seamless movement between buildings and flexible production with different industry I/O to 5G wireless network
* AI Production Line Auditing:Manual process motion detection and intelligent control without omission
* Smart Sensing:Real-time sensing of machine and pipeline abnormalities through flexible soft sensing patches
* Enterprise Intelligent Cloud Center:Based on the “IT as a Service” concept to assist enterprise to build up Intelligence Cloud Center, which supports multi- services like virtual machines, virtual desktops, container and extension to the cloud


Kaohsiung Medical University
136
0
Smart Healthcare
Arteriouvenous Fistula Inspecting and Evaluating Device
This product addresses issues faced by physicians in assessing fistula blockage, including the lack of quantifiable measurements, high costs of precise assessments, and lengthy measurement times. By using patented audio equipment and a proprietary AI model, this product enables accurate assessment of fistula blockage levels, transforming what was once a time-consuming, labor-intensive, and experience-dependent task into an efficient and reliable process.


Civil IoT Taiwan
137
0
Smart Governance
Digital Twin Technology: A Comprehensive View of Disaster Impact
The application of digital twin technology in building smart cities is becoming increasingly clear, serving as a crucial engine for driving urban transformation. In the development of smart cities in recent years, citizens can view the growth and development of the entire city, including population growth, new construction, and other major activities, in a 3D format, gradually emphasizing the concept of a virtual city. Digital twin technology can simulate disaster scenarios, including weather events and traffic accidents, assisting disaster response personnel in rapidly understanding the situation and optimizing the efficiency of disaster response. In recent years, with the advancement of aerial photography, simulation technology, and computing resources, The National Science and Technology Center for Disaster Reduction has leveraged advanced technology to create a mountainous flood inundation model system. This system enhances disaster warning and impact analysis, providing a comprehensive view of vulnerable settlements. It utilizes dynamic models and virtual-real integration, presenting alert information and disaster impacts through visual elements, contributing to informed decision-making in disaster situations.

Kaohsiung City Government
1.61k
0
Smart Transportation
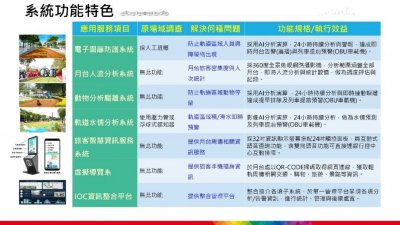
The Integration Service of Intelligent Rail Protection System
The system developed by this project provides a smart solution for station including digital fence system, platform pedestrian flow analysis, animal tracking expelled system, track water situation analysis system and platform digital information signage. The platform comprehensively analyses the image of around the station, train coordinates, passenger entry and exit, and water depth etc. Which can be used for follow up review and improvement of abnormal events such as track intrusion, crowd congestion and road flooding to achieve optimal train operation configuration and class spacing control. And provide abnormal event warning and troubleshooting and passenger intelligence information services. After the integration of multiple subsystem through the IOC platform, the system will automatically alert an alarm to the traffic control center and announce the train near the area to remind the driver to pay attention to the situation and enhance the safety of the train and the people or cars in the area when the detection system alarms.


INTELLIGENT CLOUD PLUS CO,LTD
165
0
Green Energy Trading
PowerTrade
ICP's PowerTrade integrates advanced ICT technologies to provide real-time monitoring of trading resources and execution rate calculations, enabling qualified traders to track trading conditions efficiently. PowerTrade supports resource aggregation, offering aggregators the optimal management tools to facilitate external and internal settlements.


Taiwan Intelligent Pollutant Sensing Co., Ltd.
289
0
Smart Energy Storage
E-bike Early Warning Modules for Lithium Battery Thermal Runaway
The BSMX series of early warning modules for lithium battery thermal runaway, developed by Taiwan Intelligent Pollutant Sensing Co., Ltd., is a next-generation BMS upgrade solution that requires only simple installation to integrate with existing systems. The module is equipped with high-sensitivity sensors developed specifically for energy storage safety applications, with a rapid response time of as fast as three seconds. The module offers multiple signal output interfaces to choose from and features a proprietary smart algorithm that eliminates the need for calibration after installation. It is particularly suitable for energy storage systems that operate continuously for long periods and are difficult to maintain. E-bike version has a significant improvement in power consumption.


INTELLIGENT CLOUD PLUS CO,LTD
194
0
Solar Energy
Solar
As solar generation applications continue to evolve, ensuring stable equipment operation and maximizing generation efficiency have been a main concern for owners. The platform integrates AI-driven O&M technology with precise data analysis to provide comprehensive equipment monitoring, real-time anomaly detection, and intelligent maintenance recommendations. This reduces operational costs and significantly enhances overall power generation efficiency.


Quanta Computer Inc.
71
0
Smart Healthcare
AI Telemedicine
Enables telemedicine amidst hospital, clinic, ambulance, and field settings with integrated diagnostic equipment, medical IoT devices, and smart medical glasses to allow real-time collaboration for effective remote diagnosis, in-transit patient care, and resilient health.

 、Firefox
、Firefox  、Edge
、Edge  瀏覽器!
瀏覽器!